When it comes to investigating potential insurance fraud, social media platforms can be a tremendously useful resource.
Why is Social Media a Gold Mine for Fraud Investigations?
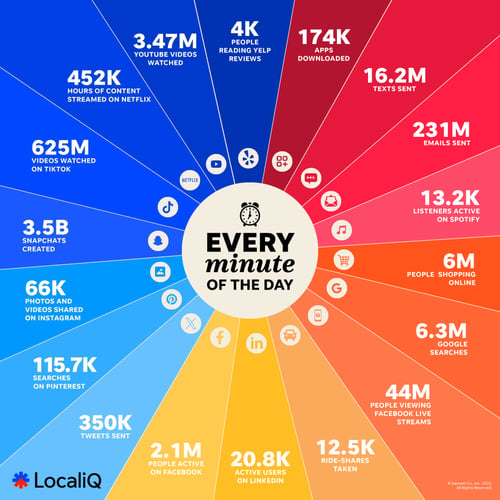
The reason for this is simple: over 5 billion of us are active on social media these days—and we tend to share more than less.
 Credit: https://localiq.com/blog/what-happens-in-an-internet-minute/
Credit: https://localiq.com/blog/what-happens-in-an-internet-minute/
In early 2024, Facebook reported three billion monthly active users, followed by Youtube with 2.5 billion users, Instagram with 2 billion, and TikTok with 1.5 billion. Even more niche platforms like Reddit have over 850 million monthly users. Not to mention the 500 hours of video uploaded to YouTube, the 350,000 tweets sent, and the 66,000 photos and videos shared on Instagram every minute!
That's a lot of potential digital evidence.
What Kind of Digital Evidence Can You Find on Social Media?
When it comes to mining social media for potential evidence, content can broadly be divided into two categories:
- Incriminating content that subjects inadvertently upload themselves: People are so used to sharing their activities on social media, that they’ll occasionally share something that incriminates them, or contradicts their legal claim, without thinking. For example, an insurance fraudster who claimed that a vehicle accident had left her severely debilitated was outed when investigators found photos of her snowboarding and scuba-diving on her social media accounts.
- Incriminating content uploaded by third parties: Just because someone isn’t very active on social media—or their privacy settings don’t allow outsiders to see much on their accounts—doesn’t mean that you can’t use social media to find useful evidence. In the case of a major car crash, for instance, it’s very possible that a bystander uploaded footage of the accident to Twitter, Facebook, or YouTube. One great example is a case where a man claimed that he’d wrecked his $60,000 Corvette while driving on the Interstate. Unfortunately for him, investigators found YouTube footage of the sports car being crashed into a barrier during a drag-racing event.
How to Use Social Media In Fraud Investigations
Of course, near-constant content creation has a major downside: because of the sheer amount of social media content out there, finding that crucial piece of evidence isn’t always easy. For this reason, social media investigations have become its own specialized field, and in order to use social media effectively for an investigation, you have to be systematic in your approach.
With that in mind, here are five tactics to use when collecting social media content as evidence during a fraud investigation:
1. Consider all the platforms
When it comes to looking for online evidence, Facebook and Instagram tend to be the most useful platforms, but others are worth considering. In fact, there are around 200 widely-used social media sites at the moment, so if you’re limiting your investigation to the top two, or three, you could be missing out on crucial evidence. For example, there was a case in 2019, during which a claim of serious physical injury was proven false with posts of a 10-mile run and a 20-mile bike ride on the fitness-oriented social media platform Strava.
2. Leverage tools to find online profiles
A simple Google search is a pretty good way of finding a particular individual’s online profiles, but other excellent tools also exist. Search tools like Pipl, Peoplefinders, PeekYou, and Classmates can all be used to identify social media profiles. If you have an image and would like to see where it appears online, TinEye is another great tool.
3. Always obtain evidence ethically and legally
It’s important to stay on the right side of the law. While law enforcement might sometimes be able to create fake social media profiles to investigate suspects, law firms and fraud investigators don’t have that same freedom. And even API tools that were once very useful for collecting social media evidence are now creating severe preservation challenges thanks to privacy concerns. So, when collecting social media evidence, focus only on content that you can view and capture legally—and use a browser-based evidence tool to collect it.
4. Consider social connections
While an individual being investigated might be clever enough to use strict social media privacy settings and refrain from posting incriminating content, they probably won’t be able to keep all their activities hidden. As mentioned earlier, a bystander might upload an incriminating video to YouTube. Similarly, someone’s friends, family, roommates, team mates, or colleagues might also post useful images and information. Because of this, it’s worth exploring the accounts of people in an individual’s social circle, as well as any pages belonging to an employer, association, sports team, etc.
5. Make sure evidence is defensible
Collecting incriminating evidence is only half the battle—legal teams also need to be able to convince other parties of the information’s authenticity. While taking a simple screenshot might seem like a quick and easy way of collecting evidence, it’s all too easy for the person under investigation (or their legal counsel) to question the quality of that content. Instead, investigators should opt for a capture method that furnishes evidence with a hash value that authenticates data and collects all the associated metadata of a social media post.
Ready to learn more? Download our Social Media and Fraud Investigations Guide below and learn how to use social media to prove fraudulent insurance claims.









