Table Of Contents
- The History of Bluesky
- Why Bluesky Matters for OSINT Investigations
- Understanding Bluesky’s Unique Architecture
- Analyzing Bluesky Profiles
- Searching for Intelligence on Bluesky
- Analyzing Bluesky Posts
- Tools for Investigating on Bluesky
- Defensible Evidence Collection
- WebPreserver for Bluesky
- Final Thoughts
The History of Bluesky
Bluesky is a decentralized microblogging social media platform similar to X (formerly Twitter). Similarities between the two platforms (including their user interfaces) are expected, as Bluesky originally began as a research initiative at Twitter in 2019 under then-Twitter CEO, Jack Dorsey.
The Bluesky initiative was created to explore the possibility of decentralizing Twitter.
In October 2021, Bluesky Social was incorporated as its own company and soon after founder Jay Graber announced their status as a for-profit public benefit LLC.
When the Bluesky app for iOS and Android launched in 2023, potential users required an invitation to register for an account. Although this limited the number of users on the platform, by the time the platform became publicly available in February 2024, the platform had over 3 million users.
Since then, the number of users has grown steadily to 38.739 million as of Q4 2025. (See Figure 1).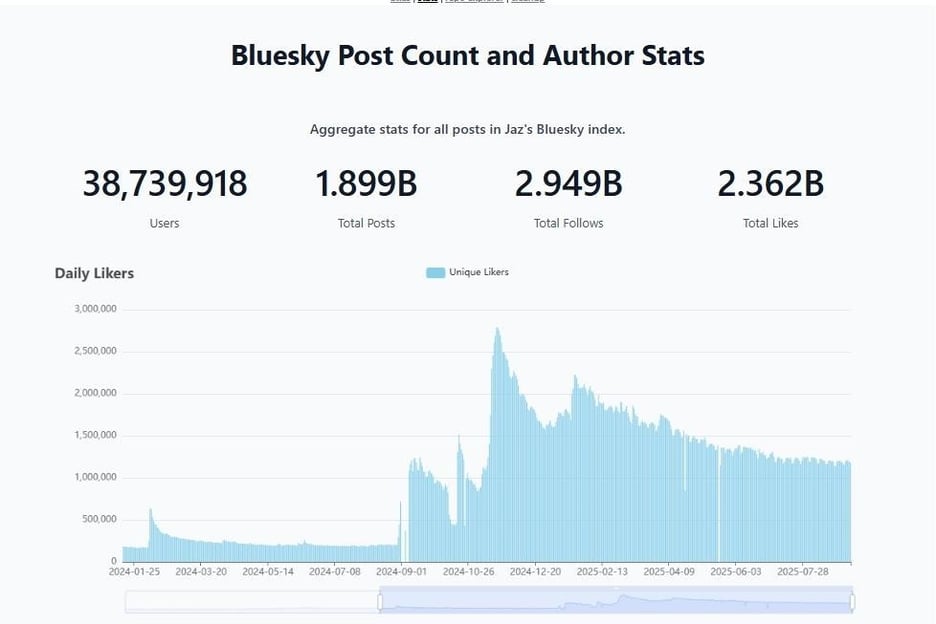 Figure 1 – Number of Bluesky users. Source: https://bsky.jazco.dev/stats
Figure 1 – Number of Bluesky users. Source: https://bsky.jazco.dev/stats
There were several sharp increases in Bluesky’s user base, usually coinciding with users taking issue with X’s new owner, Elon Musk.
In fact, there was a significant rise in Bluesky's user base after the 2024 US Election, wherein Elon Musk was president Trump’s largest individual donor. (See Figure 2) Millions of X users from around the world moved to Bluesky because of its similarities to X. Just two weeks after the US election, Bluesky reached 15 million users.
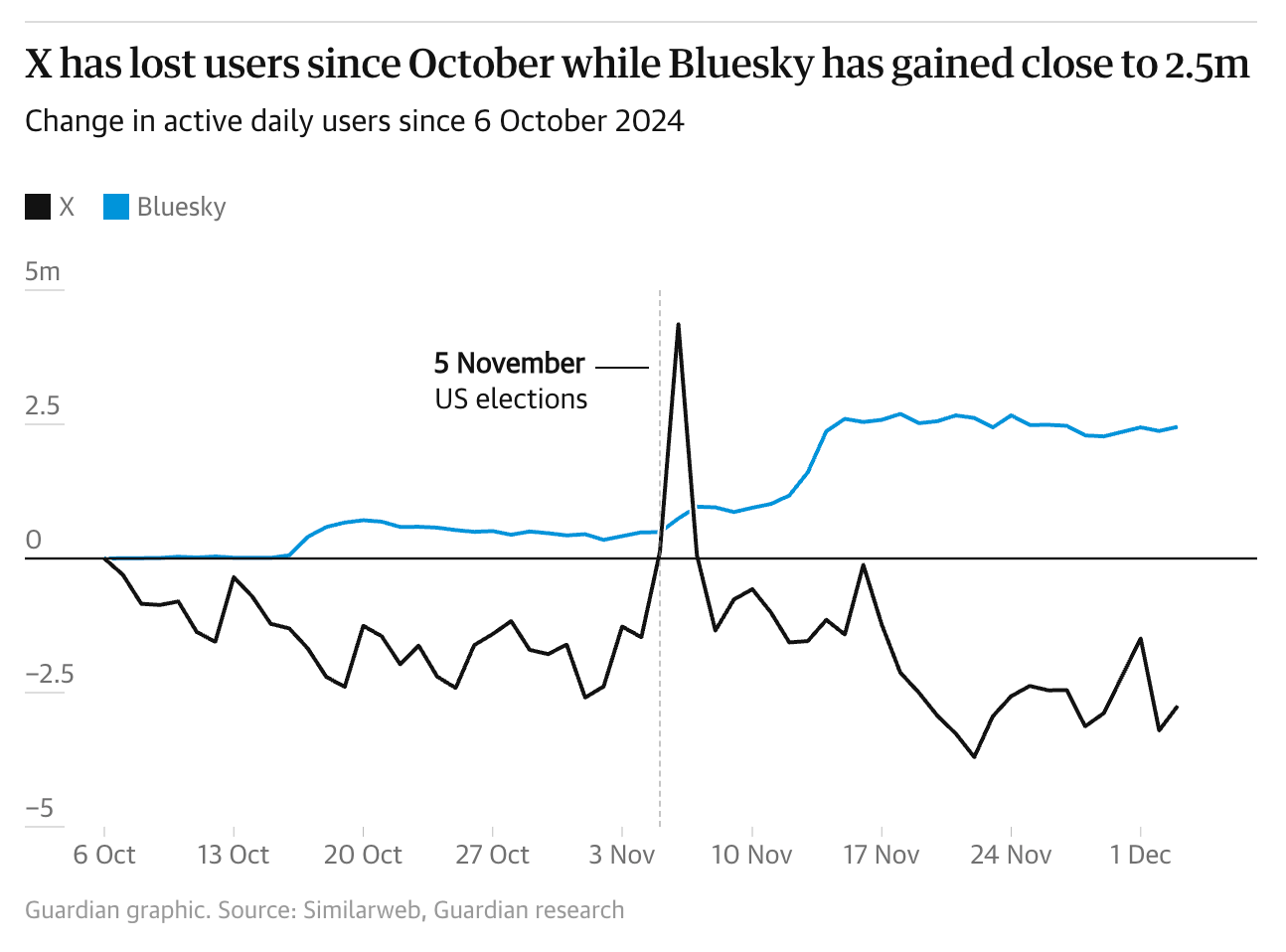 Figure 2 - X (formerly Twitter) losing users as Bluesky gains users after November 2024 US Elections.
Figure 2 - X (formerly Twitter) losing users as Bluesky gains users after November 2024 US Elections.
Source: https://www.theguardian.com/media/2024/dec/11/from-x-to-bluesky-why-are-people-abandoning-twitter-digital-town-square
Why Bluesky Matters for OSINT Investigations
Bluesky, with its AT Protocol, offers multiple advantages that simplify the work of OSINT gatherers, such as:
1. Data accessibility
Bluesky does not require authentication to start searching. Public data is available without creating an account. Investigators can browse posts, profiles, and interactions directly through the web interface.
2. Unique profile identification
By inspecting the source code of a Bluesky profile, OSINT gatherers can collect metadata such as the unique account ID (DID), profile creation date, and other technical details. The DID is essential in the Bluesky ecosystem because it allows investigators to track users even after they change their username.
3. Convert Monitoring
Bluesky’s RSS feed feature enables OSINT gatherers to follow a target's activity without visiting their profile. For example, an analyst can track all new posts of a public figure through an RSS reader, leaving no trace of monitoring activity.
4. Content Persistence
The decentralized AT Protocol architecture stores data across multiple repositories. This means deleted content may still exist on other servers and offers additional ways to recover information.
Understanding Bluesky’s Unique Architecture
Though Bluesky looks very similar to Twitter / X, it is unique among most social networking apps.
Bluesky’s AT Protocol
Bluesky is unique to most social networking apps. It has developed an open-source framework to support its system called Authenticated Transfer Protocol, or AT Protocol, for decentralized social networking. The AT Protocol is meant to give people more control over their online identity, data, and the algorithms that shape what they see. It allows users to maintain a portable identity, making it easy to move profiles and followers across platforms without losing connections. Much like email, apps built on AT can interoperate, creating a networked ecosystem rather than isolated platforms. This focus on portability and interoperability gives users more control over their data and online presence.
For example, instead of being limited to one company’s algorithm, users can select from a marketplace of “custom feeds,” each offering different ranking systems and content filters. Moderation is also decentralized, with the ability for communities or individuals to apply their own moderation services, making rules clearer and more adaptable. Together with data portability, these features ensure users aren’t locked into a single algorithm, moderation style, or provider—empowering them to shape their own social media experience.
On the AT Protocol, user identities are also tied to domain names. These domains connect to cryptographic URLs, securing the user's account and its data. Each user’s data, including posts, comments, likes, follows, media, and more, is stored in a signed data repository. These repositories act as portable, verifiable databases that can be transferred between services.
Bluesky vs. traditional social media platforms like X / Twitter
| Bluesky | VS | |
| Data Accessibility & API | ||
| Open and accessible API allowing for easier and more reliable data scraping, feed creation, and automation of searches without stringent rate limits or high costs. | Significantly restricted API access, making large-scale, automated data gathering difficult and expensive for OSINT researchers. | |
| Platform Architecture | ||
| Built on the decentralized AT Protocol. This means user data and identity are portable. For OSINT, this can create a more verifiable and persistent record of a target's activity and connections across servers. | A centralized platform. All data is controlled by one entity, which can change access rules or remove content at any time, and this can disrupt investigations. | |
| Search & Discovery | ||
| Native search is currently limited. It only searches post text and user handles. However, its open ecosystem allows for strong third-party custom feeds and search tools. | Has a strong native advanced search function. It allows precise filtering by date, engagement, and Boolean operators directly in the web interface. | |
| Media & Metadata | ||
| Users commonly upload high-resolution images and videos directly, which preserve potential EXIF data and metadata that can be used for geolocation and verification. | Heavily compresses uploaded media in addition to stripping out valuable metadata, making visual analysis more difficult. |
|
Account Structure & Identifiers on Bluesky
Understanding Bluesky's identifiers is essential for proper identity attribution and verification. As we’ve discussed, Bluesky is very different from traditional, centralized social media platform and requires a unique approach.
Bluesky Handle
Also known as usernames, a Bluesky handle has the format @username.bsky.social. It is used when mentioning someone across the Bluesky platform. It is worth noting that the .bsky.social domain is the default, but users can use their own custom domain as a handle (e.g., @osint.link).
It is essential to know that Bluesky users can change their handle at any time without losing their interactions, such as likes, shares, followers and following count. However, for OSINT gatherers, this means relying solely on the handle to identify someone on Bluesky is not reliable.
However, there is an element that does not change on Bluesky that can be used to uniquely distinguish a user: their decentralized identifier or DID.
Decentralized Identifier (DID)
The DID is a unique, permanent identifier for each account. The platform automatically generates it and cannot be changed by the user. It typically looks like: did:plc:uiovsprywx3z676npdrucizo
It is important to know that the DID is what uniquely distinguishes a Bluesky user across the platform. For instance, even if the user changes their username, display and profile pictures, their DID will still distinguish their profile.
DID is the first thing OSINT gatherers should document when investigating a Bluesky profile.
Display Name
This is what appears when a user posts or comments. It does not uniquely identify a user and can be easily changed without any implications. For instance, multiple Bluesky users can have the same display name; however, they cannot share the same username or DID identifier.
Public vs. Private Data visibility on Bluesky
A major issue that OSINT gatherers should understand about any platform before investigating is what data points are public and private. Nearly all content and profile information on Bluesky is public by design, which reflects its roots as an open social web protocol. Public information includes:
- User profile - A user's handle (username), display name, description or bio, banner image, and profile image or avatar.
- Posts ("Skeets") - Every post and its replies.
- Social graph - The lists of who a user follows and who follows them. This is important for network analysis.
- User's likes - Likes are public and can be seen on their profile page.
- Custom feeds and lists - The feeds and lists a user creates are public, showing their interests and curation patterns.
The private data includes:
- Blocked users list
- Muted users list
- Account creation date & email - This information is not publicly visible on the profile. However, we can collect the account creation date/time from the profile web page source code.
OSINT Investigations on Bluesky Profiles
Now that we understand the value of Bluesky to OSINT investigations and its unique structure we can begin our OSINT investigation on the platform.
Inspect the account DID
As we’ve learned, the DID is what uniquely distinguishes a Bluesky account. We can extract the DID of any Bluesky profile using any of the following two methods:
1. Third-party services to find DID on Bluesky
Third-party services like What's my Bluesky DID? can help you identify a user’s DID. Just enter the Bluesky handle (username), and the service will display the relevant DID identifier (see Figure 3).
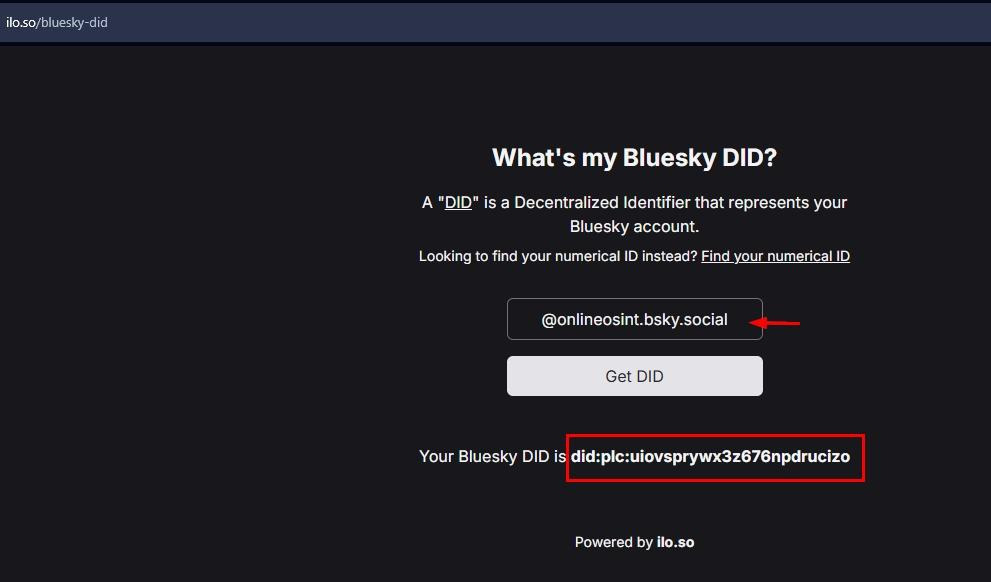
Figure 3 - Using a third-party service to retrieve Bluesky DID
2. Developer tools to find DID on Bluesky
The second method is manual and involves using the developer tools that come with the web browser to display the DID.
First, pull up the user account in question on your web browser. Right-click over the webpage, and select "inspect”.
Now go to the "Network" section, type "getProfile" in the filter, refresh the page, then select one of the network requests that loads on the left side (see Figure 4).
On the right side, select the "Response" tab, and you should see the relevant account information, including the DID underneath.
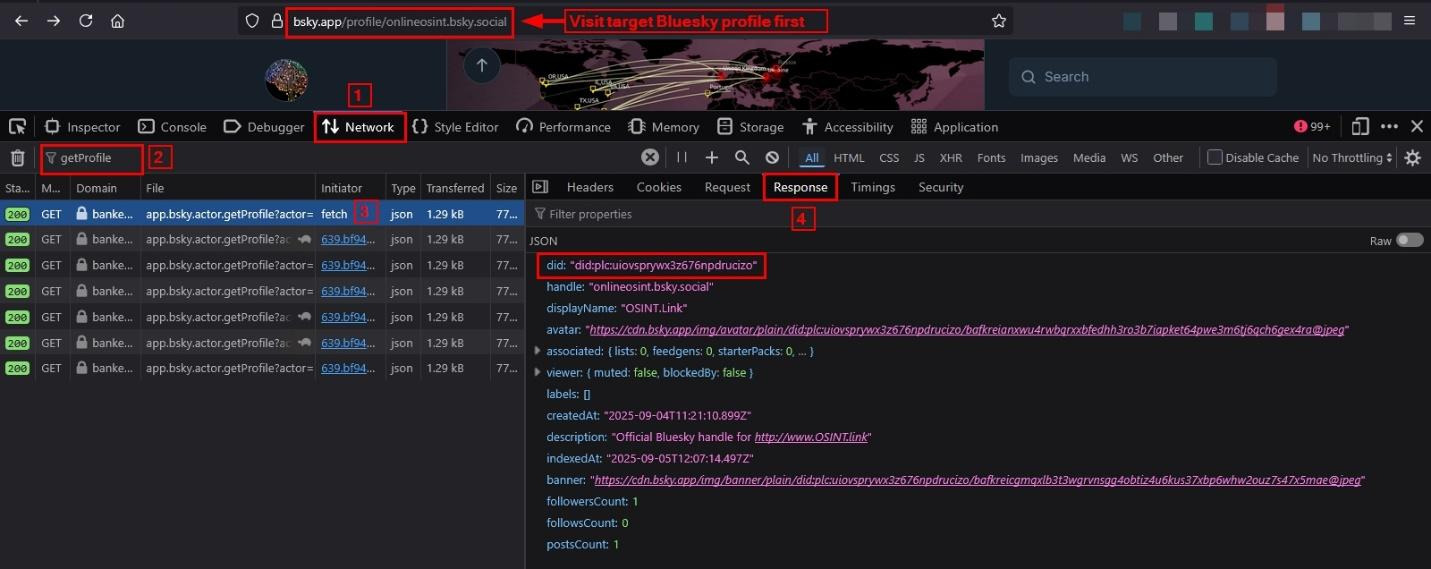
Figure 4 - Retrieving the Bluesky DID manually
Inspect the account creation date
Bluesky does not show the account creation date, but it does register the creation date/time by default. Here is how to retrieve it:
Navigate to the target Bluesky profile and open browser developer tools (F12 or Ctrl+Shift+I).
Select the Network tab and apply filters "getProfile" in the filter field. Refresh the page to capture network requests.
Click on any loaded request and examine the Response tab. Expand the user metadata fields to locate the "createdAt" timestamp (See Figure 5). This field displays the precise account creation date and time in ISO 8601 format, providing investigators with exact registration timing.
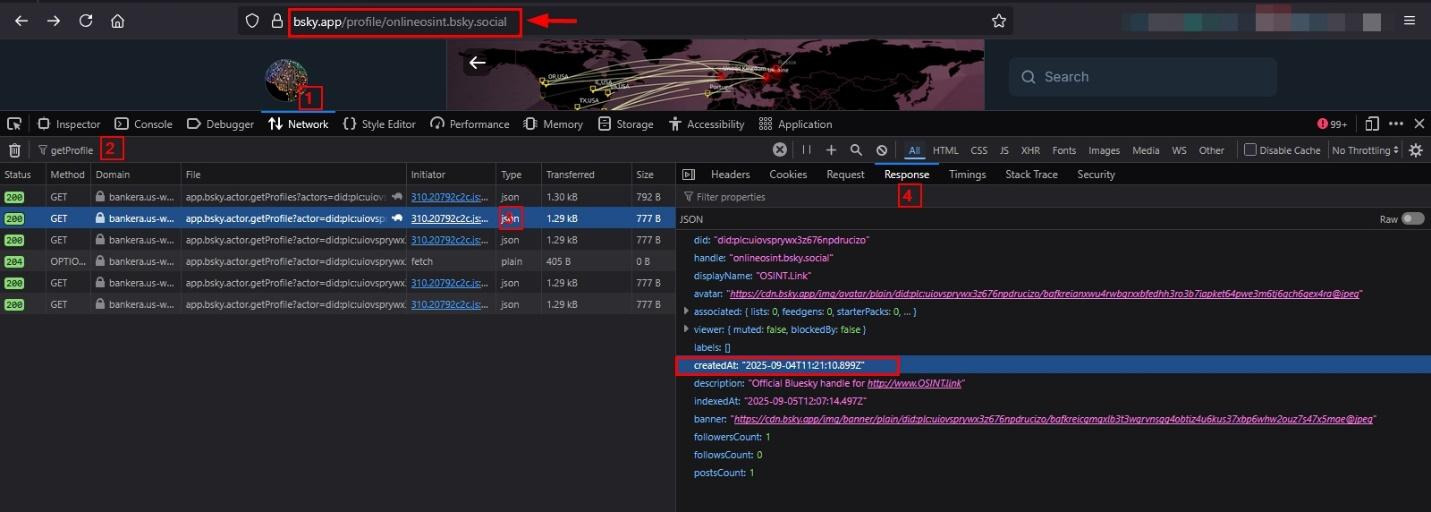
Figure 5 – Retrieve Bluesky account creation date/time
Inspect account username
Bluesky usernames are unique across the platform, but they can be changed anytime. The current username will appear in the profile URL (see Figure 6).
Username is located under the display name, it begins with @, for example: @onlineosint.bsky.social and ends with the default domain: bsky.social.
However, if the user opts to use their own domain name, then the extension bsky.social will be replaced with their domain.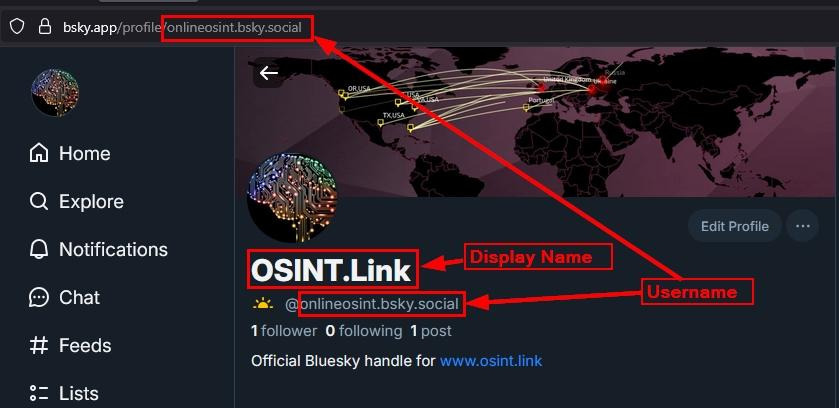
Figure 6 - Bluesky username
A Bluesky user may opt to use the same username across different social media profiles. Many users have the same username on X and Facebook as they do on Bluesky. To discover all other social media accounts on other platforms that use the same username, we can use the following services:
Inspect display name
The display name is commonly the user's first and last name. It may also point to other entities, such as a business name, favorite hobby or something else the user has chosen. It is useful to inspect the display name by searching where else it appears online, in addition to knowing the meaning behind it. For example, some names have specific cultural meanings. Here are some services to know the name's meaning:
Here are some Google dorks to search for information related to the display name (where ever else the display name is available online):
"Display Name" site:linkedin.com
"Display Name" site:facebook.com
"Display Name" site:twitter.com
"Display Name" filetype:pdf
"Display Name" "email" OR "contact"
"Display Name" "biography" OR "about"
"Display Name" "resume" OR "CV"
"Display Name" site:github.com
"Display Name" "company" OR "organization"
"Display Name" site:news.google.com
For business-related display names, check corporate registries, trademark databases, and professional licensing boards. Verify legitimacy using official business directories and regulatory filings to spot any potential impersonation attempts. Here are some resources for searching businesses:
Inspect profile and header images
Similar to most social media platforms, Bluesky allows users to have two pictures for their profile. A profile image, which could be an avatar, and a header image. For both images, we should do the following:
1. Conduct a reverse image search
Perform comprehensive reverse image searches to identify where these images appear online across different platforms and contexts. This reveals image origins, potential stock photo usage, and potentially cross-platform account correlations.
2. Inspect the metadata of images
Extract embedded metadata to reveal remnant information, including device details, geographic coordinates, timestamps, and software signatures. Here are some tools to help accomplish this:
Inspect user followers and following
A user's followers and who they follow show their digital social circles. By looking at this information, an OSINT investigator can learn a lot about the person's interests, real-world connections, job, and even where they live.
People commonly follow their real-life friends, family, coworkers, and local communities. They also follow their other owned accounts.
A cluster of followers/following from a single company or industry is a strong indicator of employment.
Bluesky allows seeing lists of followers/following of any account; all you need to do is visit the profile home page (see Figure 7). Figure 7 - View someone's followers/following
Figure 7 - View someone's followers/following
Inspect the profile bio
When OSINT gatherers inspect a Bluesky bio, they can extract more than just descriptive text, including:
- Self-declared identity - Names, aliases, or roles the user associates with themselves, such as journalist, activist, or software developer.
- Contact points - Users sometimes include their email addresses, links to their other social media platform accounts, and sometimes links to external websites, such as a personal blog or company website.
- Organizational affiliation - Users may mention companies, NGOs, political groups, or communities.
- Interests and activities - Keywords, hashtags, or causes highlighted in the bio can suggest personal or professional focus areas.
- Geographic clues - Some users openly include city, country, or regional references.
Searching for Intelligence on Bluesky
Basic search
The basic search on Bluesky is standard: you enter a keyword or hashtag in the search box located in the top right corner of the Bluesky web interface (see Figure 8). The search function is easy to find in Bluesky's navigation bar. It accepts both plain text queries and structured search operators. Results show up in real-time as you type. You will see relevant posts, users, and hashtags matching your query terms.
 Figure 8 - Bluesky search functionality
Figure 8 - Bluesky search functionality
Keyword searches
You can enter any term to find posts that contain that specific word or phrase. For example, searching "OSINT" brings up posts about OSINT topics, while "breaking news" captures urgent announcements and developing stories. The Bluesky algorithm gives priority to recent posts while keeping relevance to the search terms.
Hashtag searches
Hashtag searches use the standard format with the # symbol. Searching "#osint" reveals posts tagged with discussions about open source intelligence. In contrast, "#election2024" captures political chatter from that campaign period. Hashtag searches usually provide more focused results compared to general keyword searches.
User discovery
The search function allows you to find users by their username (handle) or display name. Entering "journalist" shows users with that term in their display names or handles. Meanwhile, searching "@username" takes you directly to specific profiles when exact matches are found.
Advanced Bluesky search
Bluesky supports adding special operators to refine our search and make it more focused. For example:
- Quotes ("phrase search") - Search for exact phrases.
- Example: "data breach" searches for the exact phrase within posts and image alt text.
- Hashtag prefix (#) - Search for posts containing specific hashtags.
- Example: #osint finds all posts with that hashtag. Try #cybersecurity for threat intelligence or #leaks for whistleblower content.
- from:username - Find posts from specific users.
- Example: from:onlineosint.bsky.social shows posts from that account.
- to:username or mentions:username - Find posts mentioning particular users.
- Example: mentions:onlineosint.bsky.social shows posts tagging that account.
- mentions:me - Shows posts mentioning your username when logged in.
- domain:website.com - Find posts linking to specific domains.
- Example: domain:osint.link shows posts linking to osint.link content (see Figure 9).
- Paste full URLs - Search for posts sharing identical URLs. Example: osint.link
- lang:code - Search posts in specific languages using two-character ISO codes.
- Example: lang:ru "OSINT" Finds posts discussing OSINT in the Russian language.
- since:YYYY-MM-DD and until:YYYY-MM-DD - Find posts within specific timeframes using UTC format.
- Example: since:2024-01-01 until:2025-08-31 "OSINT" tracks OSINT posts within this timeframe.
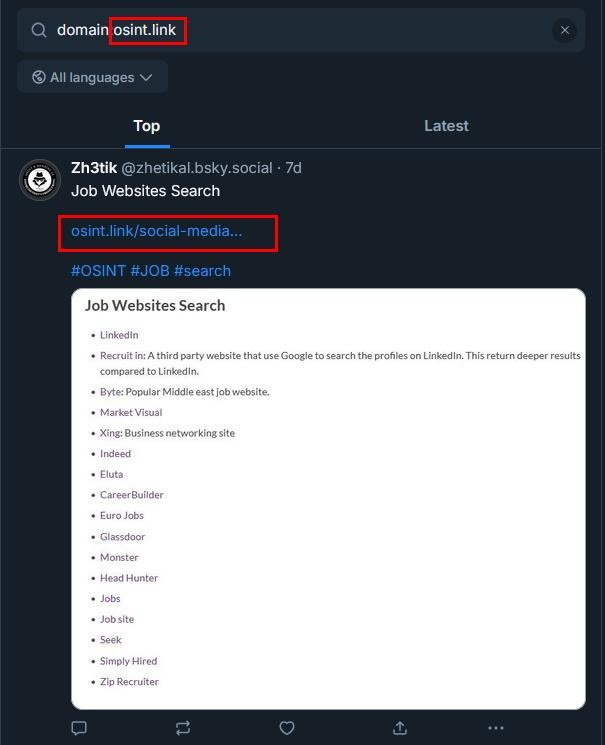 Figure 9 - Use the Domain search operator to find all posts mentioning that domain name
Figure 9 - Use the Domain search operator to find all posts mentioning that domain name
Using Google dorks to search on Bluesky
Although Bluesky is still smaller than other social networks, Google indexes its content. OSINT gatherers can use specific Google search operators to filter and extract data on Bluesky. These queries can range from simple keyword searches to more complex filters that reveal deeper connections.
- Search by keyword in bios: site:bsky.app "cybersecurity researcher"
- Finds users who describe themselves as cybersecurity researchers.
- Identify users from a specific city: site:bsky.app "New York" bio
- Discover profiles mentioning a city in their bio or within their posts.
- Track work affiliation: site:bsky.app "BBC" OR "cnn.com"
- Find users linking to specific companies or domains in their bio or posts.
- Find external links in bios & posts: site:bsky.app "github.com"
- Reveal users linking to GitHub profiles, useful for cross-platform tracking.
- Search for potential whistleblowers or leaks: site:bsky.app "confidential" OR "leaked document"
- Identify posts containing sensitive claims.
Analyzing Bluesky Posts
Posts are central to user activity on Bluesky and often serve as the most valuable starting point for OSINT investigations.
By looking at what users publish, how they interact, and the external content they share, OSINT investigators can reveal behavioral patterns, networks of influence, and hidden identifiers.
Analyzing users’ posts needs to go beyond surface-level and include analyzing links, media, and the technical traces left in each post.
Analyzing post content
- Language and tone – Inspect writing style, choice of words, and recurring writing themes to identify personal, political, or professional leanings.
- Hashtags and keywords – Extract hashtags or repeated keywords to reveal areas of interest, affiliations, or the online campaigns the user commonly supports or cares about.
- Posting patterns – The frequency, time zones, and active hours may provide clues about geographic location or daily routines.
- Engagement patterns – Replies, mentions, and interaction patterns can map a user's social circle and highlight influential connections.
Analyzing links and embedded media
- External links – Posts may sometimes contain references to external domains, such as news outlets, GitHub, or Substack. These can lead to secondary accounts or confirm the professional activities of the target.
- File and media analysis – Images, videos, or attached files may hold metadata, including EXIF data, or visual details that are useful for geolocation and verification.
- Shortened URLs – Bluesky users sometimes share shortened links. Expanding these can reveal the original domain.
- Cross-platform connections – Embedded media from other platforms, like YouTube, TikTok, or Instagram, can provide direct leads to additional accounts to investigate.
Tools for Investigating on Bluesky
Searching Bluesky effectively will require moving beyond the platform's built-in features. While the native search lets you look up basic keywords and profiles, OSINT investigations often need deeper filtering and better data correlation.
A growing number of third-party tools and online services now support Bluesky. These tools allow investigators to analyze posts, monitor accounts, map networks, and connect different datasets with more precision.
WebPreserver is a browser plug-in that allows investigators to automate evidence and intelligence gathering, including scrolling long timelines and feeds. All evidence captured with WebPreserver is digitally-signed to ensure it hasn’t been tampered with, contains all important metadata and is presented in native context so it will stand up in court.
Bluesky post analyzer allows you to conduct detailed analysis on Bluesky posts such as tracking likes, reposts, replies and quotes. It also allows viewing timelines, user interactions and performance metrics (see Figure 10).
Bluesky Join Date Checker can help you quickly find Bluesky users’ join date/time.
Bstat tracks Bluesky profile statistics, such as the number of followers, follows, skeets, likes, and reposts.
Dopplersky allows you to track Bluesky profile stats, posts, and follower growth.
Bskyinsights is another service that provides insights on any Bluesky profile.
Blueskymeter is a service that displays user analytics.
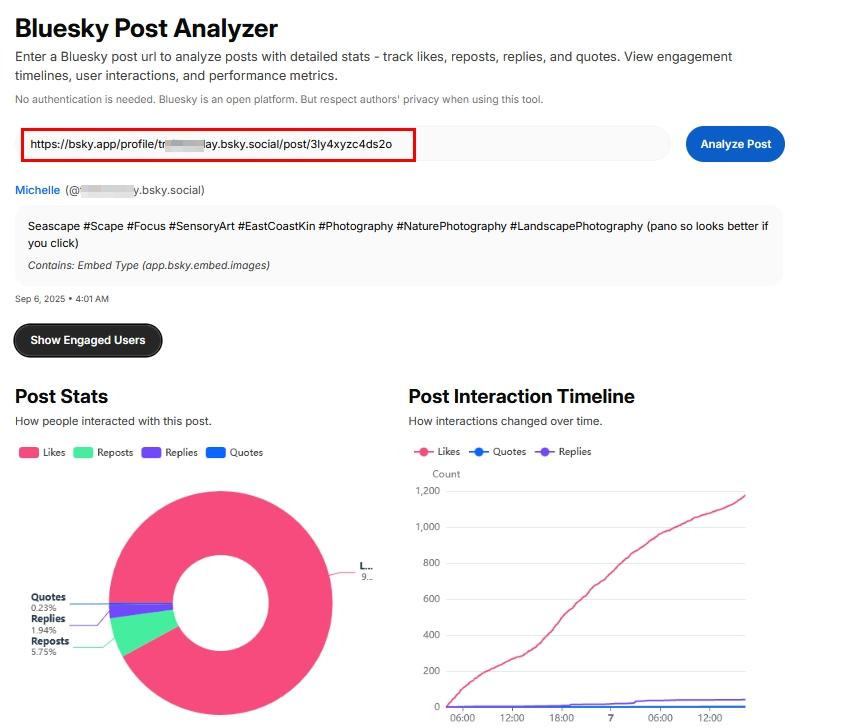 Figure 10 - Bluesky post analyzer
Figure 10 - Bluesky post analyzer
Defensible Evidence Collection on Bluesky
As we’ve demonstrated, Bluesky is a valuable source for collecting intelligence and digital evidence.
However, because evidence on any social media site can disappear without notice, OSINT investigators should follow specific procedures when collecting evidence to ensure the defensibility of their findings:
- Capture screenshots of relevant posts and comments, including timestamps and metadata, before they get deleted by the target user/s.
- NOTE: Screenshots may not be defensible in court unless they include proper metadata, context, hyperlinks and can be authenticated as genuine and unaltered. To capture this data in an authenticated format, consider using a web evidence capture tool like WebPreserver.
- Document the search process including the keywords used and the date/time when the evidence was captured to establish a transparent chain of custody.
WebPreserver for Bluesky Investigations
WebPreserver is a social media and web capture tool that allows you to capture Bluesky posts, comment threads, or entire profiles and timelines in just a couple of clicks. The browser plug-in automatically expands threads and comments, and autoscrolls timelines, saving you time from manually expanding and capturing every post.
Better yet – all evidence collected is complete with the appropriate metadata, digital signatures for authentication, and can be exported in native formatting, so you can present your evidence in context.
Bluesky OSINT: Final Thoughts
Bluesky is quickly becoming a meaningful source for open-source intelligence. Its AT Protocol gives investigators unique benefits due to its verifiable identities (DIDs), open architecture, and variety of publicly accessible data. This creates an opportunity to dive deeper than what’s possible on older, closed platforms.










