With the rise of social media, individuals have become increasingly comfortable sharing personal information online. However, this has also made them susceptible to social media impersonation, a growing phenomenon that can lead to identity theft and other online fraud. Impersonators can easily create fake profiles and use stolen personal information to deceive others. They may use this information to gain access to private accounts or even steal money.
What is Online Impersonation?
Online impersonation, a cybercrime where perpetrators create fake social media profiles using stolen personal data to deceive unsuspecting victims, has become increasingly prevalent with the rise of social media. Cybercriminals and scammers aim to make these profiles appear genuine and trustworthy, putting individuals and even large-scale organizations at risk of financial loss and damaged reputation. This cybersecurity issue should not be taken lightly, as the consequences of a successful campaign can be dire.
5 Types of Online Impersonation
It's important to be aware of the most common types of social media impersonation when interacting with people and organizations on your preferred social platforms.
1. Personal Account Impersonation
The abundance of personal information available on social media has presented scammers and cybercriminals with a treasure trove of resources for constructing authentic-looking fake profiles. This type of impersonation is what usually leaps to mind, as it can cause significant financial losses and reputational harm to the victim.
2. Social Media Account Hijacking
Hackers can gain access to a genuine social media account and use it to disseminate false information, damage relationships, and hurt the victim's reputation. This type of impersonation is particularly prevalent among social media influencers who have a large following, as scammers see them as prime targets for their malicious activities. Social media hijacking can also lead to financial loss, as scammers may use the victim's account to promote fraudulent schemes or solicit donations from unsuspecting followers. In addition, victims of social media hijacking may find it difficult to regain control of their accounts, leading to ongoing damage to their online presence and reputation. It is important for social media users to take steps to protect themselves from these types of attacks, such as using strong passwords, enabling two-factor authentication, and being vigilant about suspicious activity on their accounts.
3. Bot Accounts
Bot accounts provide cybercriminals with the ability to impersonate their victims and automate a variety of online tasks, enabling them to scale up their operations and victimize even more people. What makes this type of social media impersonation so dangerous is that scammers can run multiple scams simultaneously, constantly profiting off at someone else's expense.
4. Executive Impersonation
Executive impersonation is a growing concern for businesses and individuals alike. Cybercriminals often pose as high-ranking personnel in a victim's company to gain access to sensitive data or financial information. These scammers are becoming increasingly sophisticated in their methods, with many using social engineering techniques to deceive their targets. One of the reasons for the rise in executive impersonation is the ease with which social media platforms can be exploited. Twitter's new $8 blue verification checkmark, which is designed to verify the authenticity of high-profile accounts, has been abused by scammers who create fake celebrity and company accounts to trick unsuspecting victims.
5. Brand Impersonation
Brand impersonation is a fraudulent act where cybercriminals steal a company's identity to deceive its followers. They aim to redirect traffic to a phishing page, hoping that users will mistakenly enter their personal information thinking the page is genuine. To further deceive their targets, scammers may also run false ad campaigns and respond to customer inquiries, creating a false sense of trust.
The Growing Trend of Social Media Impersonation
The proliferation of social media impersonation comes as no surprise, given the various factors that make it easier for fraudsters to deceive their targets. Here are the top three reasons why this trend is unlikely to slow down anytime soon.
1. A Wealth of Public Information
This abundance of public information on social media platforms is a goldmine for scammers looking to impersonate individuals. They can easily access details such as birthdates, addresses, and even employment information, which can be used to create authentic-looking fake profiles. To make matters worse, scammers can also purchase followers, likes, and comments to make their fake accounts seem even more legitimate.
In addition, sophisticated tools (think ChatGPT) now allow them to imitate their victim's writing style, making it nearly impossible for the average user to detect fraud. As a result, victims may unknowingly engage with these fake accounts, sharing sensitive information, and falling prey to financial scams.
2. Content Blends In
With the rise of social media impersonation, cybercriminals have become increasingly adept at blending their fraudulent activity into the natural flow of social media feeds. They know that people are quick to trust others online and are constantly looking for ways to make their fake profiles appear as authentic as possible. From mimicking writing styles to purchasing followers and comments, scammers use every tool at their disposal to make their activity blend in with legitimate content on social media.
3. Users Relax on Social Media
Social media platforms are designed to be entertaining and engaging, encouraging users to spend more time scrolling through their feeds and interacting with others. However, this relaxed atmosphere can also make users vulnerable to social media impersonation. When users are in a relaxed state of mind, they tend to let their guard down and may not question the authenticity of the content they encounter. This can lead to unwittingly sharing personal information or engaging with fraudulent accounts.
4. Official Accounts Are Often Moderated by Multiple Users
Scammers can exploit the fact that official social media accounts are often managed by multiple employees to hack into those accounts and impersonate the owners.
Scammers often start by conducting research to gather information about the target and the organization they work for. They may search for publicly available details, such as the target's name, job title, email address, or any personal information shared online.
Scammers may use phishing techniques to trick an employee who has access to the official social media account into revealing their login credentials. They might send a convincing-looking email or message that appears to be from a legitimate source, such as the social media platform or the company's IT department. The message could contain a request to verify account details, change passwords, or perform some urgent action that prompts the employee to provide their login information unwittingly. If scammers are successful in tricking an employee into divulging their login credentials, they gain access to the official social media account. In some cases, scammers may use keyloggers or other malware to steal login information directly from the employee's computer.
With the obtained login credentials, scammers can log into the official social media account. Since these accounts are often managed by multiple employees, it can be challenging for the legitimate account owner to notice unauthorized access immediately. Once scammers gain control of the official social media account, they can impersonate the legitimate account owner or the organization itself. They may change profile details, post misleading information, send messages to followers, or engage in fraudulent activities while appearing to be the genuine account owner.
Examples of High-Profile Online Impersonation Cases
Here are three high-profile online impersonation cases and a short description of the events that unfolded and what happened to the scammers.
2020 Hacked Celebrity Accounts
In 2020, one of the biggest online impersonation cases occurred when a group of hackers gained access to the verified accounts of some of the world's most powerful individuals and companies, including Apple, Elon Musk, Bill Gates, Warren Buffet, Jeff Bezos, Joe Biden, and Barack Obama. The hackers then used these accounts to promote a cryptocurrency scam, causing widespread panic and confusion among their millions of followers.
The scam claimed that anyone who sent Bitcoin to a certain address would receive double the amount in return, but in reality, the hackers stole the Bitcoin and disappeared. This incident highlighted the vulnerability of even the most secure online accounts and the ease with which cybercriminals can cause significant financial damage and reputational harm.
Twitter’s $8 Blue Check Mark
In November 2022, Twitter decided to change its policy on its famous blue verification check marks; with a small fee of $8, anyone could become instantly verified. The result was pure chaos, causing massive global companies to lose large amounts of potential revenue, all because Twitter made it possible for anyone to impersonate anyone else.
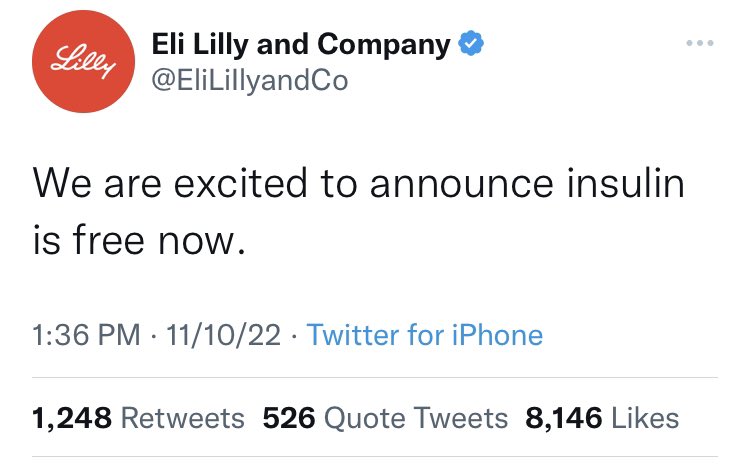
Twitter caused much trouble for many companies, many of whom have left the social media platform for good due to this online impersonation scandal. One of these companies, Eli Lily, lost millions in ad revenue simply because an impersonator published on Twitter that the company was now giving away all insulin for free.
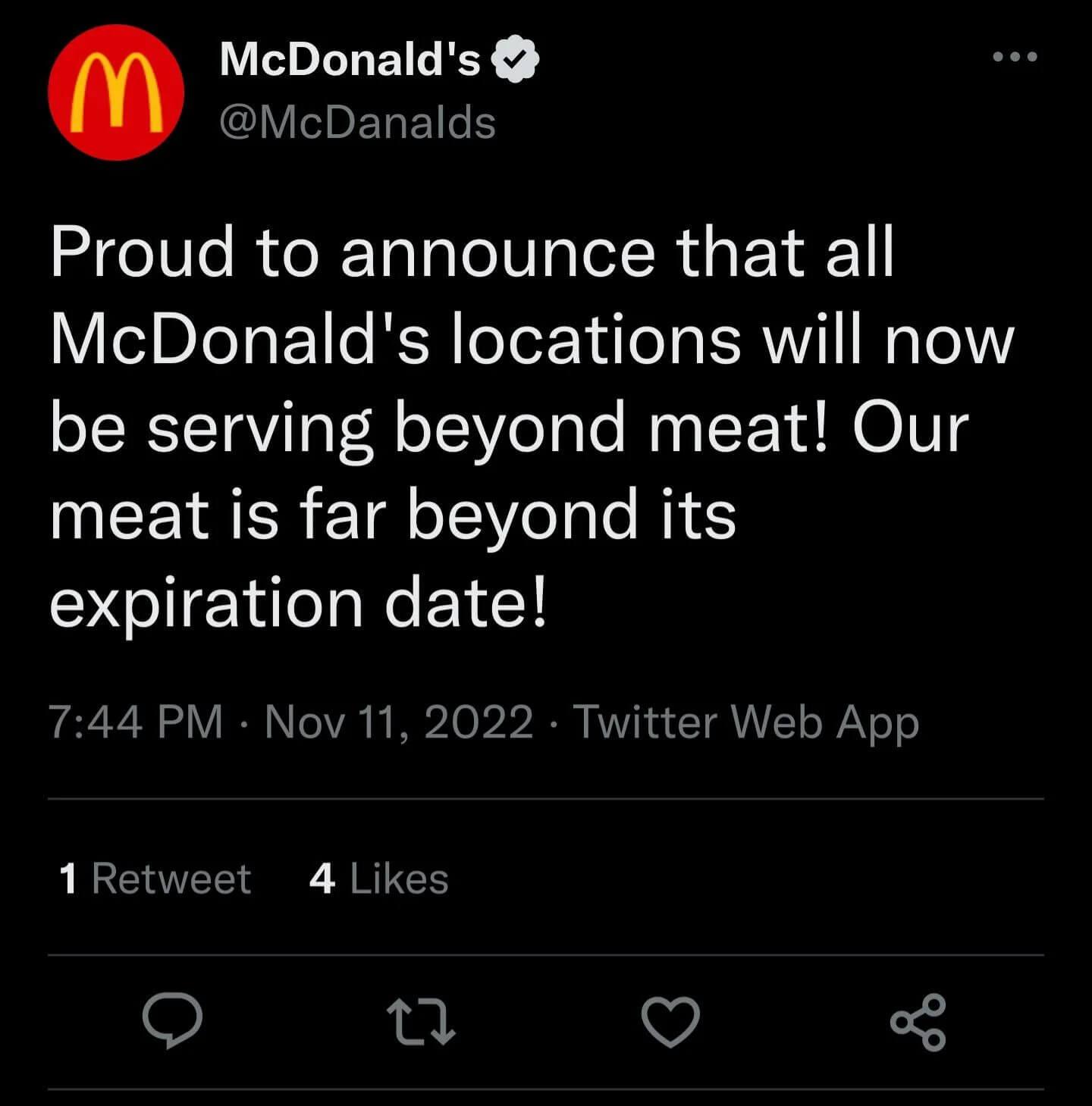
Eli Lily was not the only company dealing with impersonators; McDonald's had copycats posting that they were "proud to announce that McDonald's locations will now serve beyond meat! Our meat is far beyond its expiration data!"
Tiger Woods
Celebrities are not immune to online impersonation, as demonstrated by pro golfer Tiger Woods' experience in court in 2000. A man named Anthony Lemar Taylor stole Woods' social security number and applied online for credit cards in the athlete's name, resulting in charges totaling $17,000. Taylor received a 200-year sentence due to prior charges, highlighting the severity of online impersonation and its potential consequences.
Kim Kardashian
In 2014, a 19-year-old named Luis Flores Jr. used Kim Kardashian's stolen identity to apply for credit cards with American Express, changing her social security number and address to his own. Flores had also collected personal information on high profile figures such as Bill Gates, Michelle Obama, Joe Biden, and Beyoncé. The police discovered that he had committed fraud against U.S. Marshals Service Director Stacia Hylton and former FBI director Robert Mueller. As a result, Flores was sentenced to three-and-a-half years in federal prison.
Kenneth Gilbert Gibson
In 2022, Kenneth Gilbert Gibson masterminded a scheme that involved setting up more than 8,000 fake PayPal accounts using stolen identities. During the investigation, authorities discovered that Gibson had used an automatic script to create these accounts, using data obtained from employees and customers at his day job. He allegedly managed to accumulate $3.5 million through fraudulent transactions by conducting small transactions to avoid detection. Most of his victims were unaware of the identity theft until they tried to obtain loans or deal with collection agencies. Gibson was eventually sentenced to four years in federal prison for wire fraud, mail fraud, filing a false tax return, and aggravated identity theft in 2018.
How Scammers Hack Your Accounts
Credential stuffing is a popular method among cybercriminals, allowing them to gain access to social media accounts by using login credentials obtained from data breaches on other platforms. This method works effectively because many users tend to reuse the same password across multiple websites and accounts. The hackers use automated tools that test thousands of username and password combinations at once, making it a quick and efficient method of attack. Once they gain access, the hackers can cause significant damage, including identity theft, financial loss, and reputational harm.
To protect yourself from credential stuffing, it's crucial to use unique and strong passwords for each platform and website. A strong password should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and special characters. Additionally, enabling two-factor authentication adds an extra layer of security to your accounts, making it much more challenging for hackers to gain access, even if they have your password. Two-factor authentication requires a second form of authentication, such as a fingerprint or a code sent to your phone, to verify your identity.
While creating unique and strong passwords and enabling two-factor authentication may seem like a hassle, it's a small price to pay for the peace of mind that comes with knowing your online identity is secure. By taking these simple steps, you can significantly reduce your risk of falling victim to social media impersonation and other forms of cybercrime. Remember, securing your online identity is not just about protecting yourself; it's also about protecting your friends, family, and colleagues who may be vulnerable to cybercriminals.
How Scammers Impersonate You Online
Scammers can impersonate individuals online in various ways, often using deceptive tactics to trick others into believing they are the person they are impersonating. Here are a few common methods scammers may employ to impersonate you online:
-
Social engineering: Scammers may gather information about you from various sources, such as social media profiles or public databases. With this information, they can impersonate you by creating fake accounts or sending emails pretending to be you. They may also manipulate others into revealing personal information about you, further enabling their impersonation efforts.
-
Phishing: Scammers may send fraudulent emails or messages that appear to be from you. These messages typically include links to fake websites designed to steal personal information or login credentials from unsuspecting victims. By impersonating you, scammers try to establish trust and convince others to disclose sensitive information.
-
Identity theft: If scammers gain access to your personal information, such as your name, address, social security number, or bank account details, they can assume your identity online. This can be done through data breaches, hacking, or by purchasing stolen information on the dark web.
-
Account takeover: Scammers may try to gain unauthorized access to your online accounts, such as email, social media, or financial accounts. Once they gain control, they can impersonate you by sending messages, making posts, or engaging in fraudulent activities under your name.
-
SIM swapping: Scammers may target your mobile phone number by contacting your service provider and convincing them to transfer your number to a new SIM card under their control. This allows them to intercept verification codes sent via SMS, gaining access to your accounts and impersonating you.
How to Prevent Online Impersonation
Online impersonation can cause significant financial damage and reputational harm, making it crucial for individuals and companies alike to take steps to prevent it. Here are some additional tips on how to prevent online impersonation:
- Implement Strong Password Policies: To prevent credential stuffing, companies should implement strong password policies that require employees and customers to use unique and complex passwords for each account. Passwords should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and special characters. Additionally, companies should encourage employees and customers to use password managers to store and generate strong passwords.
- Use Multi-Factor Authentication: Multi-factor authentication adds an extra layer of security to online accounts, making it much more challenging for hackers to gain access, even if they have your password. Two-factor authentication requires a second form of authentication, such as a fingerprint or a code sent to your phone, to verify your identity.
- Monitor Your Online Presence: Companies should regularly monitor their online presence to identify any instances of online impersonation. This can be done using online reputation management tools that scan the internet for mentions of the company's name, products, or employees.
- Educate Employees and Customers: Companies should provide regular training to employees and customers on how to identify and prevent online impersonation. This can include teaching them how to spot phishing emails, how to use multi-factor authentication, and how to report suspicious activity.
- Report suspicious activity: If you believe someone is impersonating you online, report it to the relevant platform or website. You can also consider filing a complaint with your local law enforcement agency.
- Don't contact the impersonator: It's natural to want to confront the person impersonating you online, but it's important to resist the urge. These fraudsters are skilled at manipulation and can easily take advantage of your emotions. Instead, report the incident to the relevant platform or website and consider filing a complaint with law enforcement. Taking these steps can help prevent further damage and protect yourself and others from falling victim to cybercrime.
By implementing these tips, individuals and companies can significantly reduce their risk of falling victim to online impersonation and other forms of cybercrime. Remember, prevention is key when it comes to online security, and taking proactive measures is always better than dealing with the consequences of a data breach or identity theft.
Online impersonation and social media abuse often go hand-in-hand. Read our article below to see how you can protect yourself against online abuse and harassment.