Ransomware attacks are on the rise, but sophisticated dark web forensics and tools are helping investigators to transform the dark web from a murky and lawless online environment, into a treasure trove of evidence and information.
In the 1900s, organised crime was personified by Al Capone, Frank Costello and John Gotti — infamous names that are still known today, even though they operated in a limited geographical area.

Thanks to the dark web, 21st century organised criminals have gone global — and they are targeting anyone from small businesses to multinational enterprises. They operate from the shadows behind crime syndicates with names like REvil, DarkSide and Evil Corp, and they’re democratising cybercrime. Ransomware can be bought on the dark web for as little as US$100, which means criminals don’t need to be skilled hackers to launch a cyber-attack.
It’s an extremely profitable business model. According to the 2021 SonicWall Cyber Threat Report, ransomware attacks rose by 62% worldwide between 2019 and 2020.
The IBM X-Force® Threat Intelligence Index lists ransomware attacks as the top threat in 2020, making up 23% of all attacks. In fact, the report estimates that REvil, a criminal malware group that also takes a cut of its affiliates’ earnings after a successful malware attack, conservatively made a profit of USD 123 million in 2020 thanks to do-it-yourself ransomware-as-a-service (RaaS) tools that anyone can access on the dark web – provided they know where to look.
The dark web and the rise of ransomware attacks
First, it’s important to understand that there are three layers to the web.
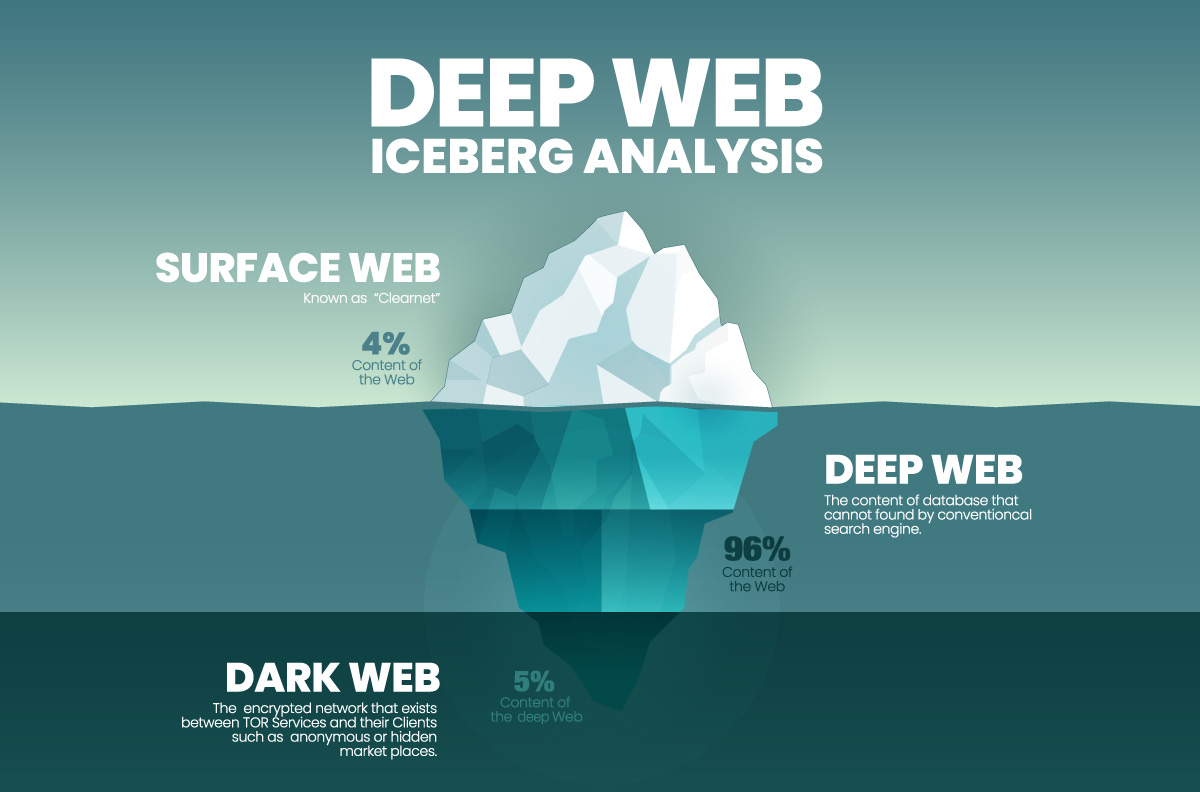
The surface is the public web. It makes up about 4% of the total Internet. If you can use a search engine to find information or a website, it’s been indexed and is on the public web. The next layer is the deep web, which makes up approximately 96% of the Internet. This is anything online that requires a username and password to access. The deep web encompasses everything from social media profiles and Slack chats to banking profiles and confidential medical information. You won’t find deep web information through a Google search. Instead, you’ll need a specific link and the right credentials to access specific sites, platforms and data.
And then there’s the dark web. The dark web can only be accessed through special software, such as The Onion Router (also known as the Tor network). Nothing on the dark web is indexed, and it’s difficult to navigate even if you can gain access, because you will need to find a .onion site’s address on your own, and these tend to be a long string of random letters and numbers. The software to access the Tor network is free to download, however, which technically means that anyone can access the dark web.
Interestingly, the dark web was not designed for illegal activities. In fact the U.S. Naval Research Laboratory developed the Tor browser itself in the 1990s. It’s original purpose was to conceal the identities of American operatives working overseas, as well as dissidents attempting to communicate from within oppressive regimes. In 2002 the browser was released to the public, and since then it has been used to protect the anonymity of users for multiple reasons, including by journalists working internationally who need to protect their identities.
These multiple layers of encryption ensure that people can browse the dark web and post information with near anonymity, which is why it’s not surprising that it’s become the go-to platform for buying and selling illegal services and goods – and why dark web investigations and dark web forensics have become so important. As ransomware groups continue to emerge and dark web marketplaces thrive, the ability to investigate and shut down illicit transactions remains crucial.
Investigating the dark web
On May 7, 2021, Colonial Pipeline was forced to proactively shut down operations as a result of a ransomware attack. Since Colonial Pipeline is responsible for nearly half the fuel supply for the US East Coast, the Federal Engine Carrier Safety Administration (FMCSA) declared a state of emergency in 18 states to help with the shortages of gasoline, diesel, jet fuel, home heating oil, and military supplies that were the result of the shutdown.
By the fifth day of the shutdown, 30% of petrol stations in metro Atlanta were without gasoline, and other cities were reporting similar numbers.
The FBI confirmed that DarkSide, a cybercriminal group believed to have originated in Eastern Europe, was behind the attack thanks to (you guessed it) Ransomware as a Service (RaaS) software.
Dark web digital forensic teams were able to investigate the hack and track down DarkSide’s servers through the Bitcoin ransom payment made by Colonial Pipeline to the criminal syndicate.
In fact, in June 2021, the U.S. Department of Justice announced that, thanks to its dark web digital forensic teams, it had recovered $2.3 million worth of Bitcoin that Colonial Pipeline paid to DarkSide in May.
In response to the seizure, DarkSide disbanded and issued a farewell message to its affiliates on 14 May, saying its Internet servers and cryptocurrency stash were seized by unknown law enforcement entities.
The Challenges of Dark Web Investigations
Recouping $2.3 million worth of Bitcoin was a win for the FBI, but investigations into the dark side of the Internet remain challenging, not least of all because the dark web is designed to ensure anonymity and reduce traceability. Collecting evidence from a website on the surface web or an account on a popular social media site is relatively simple, but collecting evidence on the dark web requires a high level of technical know-how, as well as sophisticated collection tools.
The good news is that while the dark web is not an environment that lends itself to typical online investigation methods, if you do have access to the right forensic preservation tools, it can offer incredible opportunities for conducting online investigations and collecting evidence.
By leveraging modern solutions, investigators can transform the dark web from a murky and lawless online environment, into a treasure trove of evidence and information.
Learn how you can access the dark web and collect evidence from it in this Dark Web Investigations paper.








